
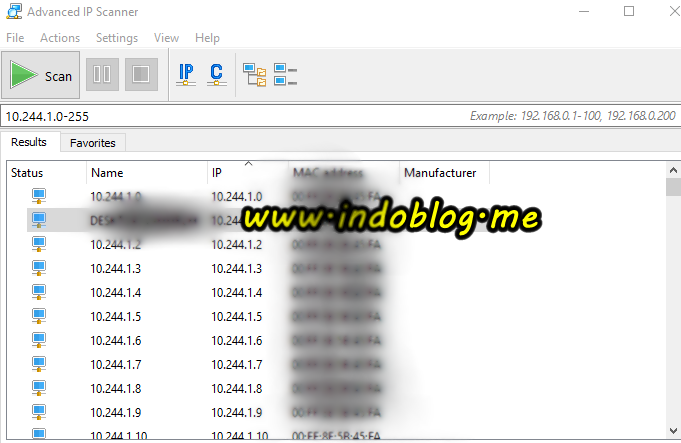
Cara Masuk Komputer Orang Lain Dengan Cmd Command
CARA MASUK KOMPUTER ORANG LAIN DENGAN CMD/MSDOS - Kali ini saya akan memberikan sedikit informasi tentang seseorang yang ingin mencoba menerobos masuk ke komputer orang lain melalui DOS(Windows XP/2000).Hal yang pertama kita lakukan adalah kita harus tahu dulu alamat IP address/Host Name/Computer name target/korban: berikut langkah-langkah nya: 1.
Tulisan ini hanya berdasarkan kebutuhan saya saja dalam bekerja agar tidak lupa, jika mau dikembangin lagi perintah-perintah lainnya, silahkan explorasi sendiri menggunakan /help. Sebelumnya silahkan download program remote CMD PSTools. • Lagi heboh daftarin ID di 4444, yang namae penjahat, tinggal googling KTP uda bisa jadi orang jahat. • Ganti 4G tambah ancuri gini @, kangen paket data unlimited pascabayar CDMA. • Walau dunia membenci, ku kan tetap disini. Karena telahku habiskan sisa hidup dan cintaku hanya untukmu. • Tanggal 4 mulai aktif kembali jadi anak kos setelah lama pensiun.
• Allah masih beserta orang-orang yang sabar. • Hidup itu ga bisa di undo, salah setting aja uda ga bisa dibalikin ke waktu sebelumnya. • Lucu liat ortu rebutan kursi sekolah, dulu jaman SD bangku uda dipilihin guru. Pas SMP/A malah pilih sendiri dan favoritku paling belakang.
• Mbelakrak nak Mboteng. • RT @: Goollll.!!! Menit Ke 70' M. Solikin mencetak gol indah lewat tendangan bebas PSBI Blitar 1 vs 2 PERSEBAYA Untuk Kemajuanmu.
Hi My Brothers! • Wanna do some WATCH_DOGS style H4cK1nG.!!!, then you are at Right Place! • You can call it as: ' Android to Android Hacking'. This method works 100%, so follow my tutorial carefully, it is really very easy to follow ( but a bit Complicated).
If you got any errors or you think I`ve missed something, then inform me in Comments section. I`ll try best to solve the problem. • DISCLAIMER: This Thread is O.N.L.Y for Education Purposes.
I will not be Responsible of Any Negative and Illegal use of this information. Try not to HACK the Androids, other than your`s.
Or you will be in PRISON. Only Use this information for testing purposes.
So, lets get started. Requirements 1). Android 5.0 () 2). TermuX Android App (Download it from 3). Installed Metasploit Framework in TermuX () 4). Active Internet/WiFi Connection 5).
TermuX should be allowed to use External Storage (For this only enter this command only at once: 'termux-setup-storage') 6). MiXplorer (For signing APK file, Download it from ) 7). MiX Signer (APK Signer for MiXplorer, Download it from ) 8).
(Recommended) Use for entering commands in TermuX easily. Step 1: Port Forwarding • Many People use NGROK for Port Forwarding. But in NGROK, you can see that it always generates a new Domain or Port when you Re-connect to it. Reserved Domain and Port is Unfortunately only available for PAID or their Premium Costumers. That is why, for NGROK you have to generate a new APK file every time you start hacking. We are gonna use.
In Serveo, you can manually forward your desired port on Internet (and can forward it again in future). To use Serveo Port Forwarding, you have to install OpenSSH package for TermuX. For this, enter this command in TermuX: pkg install openssh — It will successfully install OpenSSH • After installation, just type this: ssh -R (Desired_Port):localhost:(Desired_Port) serveo.net — • It may ask you about default ssh or something like this. Just type 'yes' when it ask about it. • Here, you have to keep some points in mind; IF you want to forward an HTTP Port, then select different ports in both 'Desired_Port' fields. But here we gonna forward a TCP port.
To forward TCP port, you have to enter same, desired ports in 'Desired_Ports' field. Also, do not change 'localhost'. Here we are going to Forward a TCP port: 4564 (just for an example).
After forwarding port, it may look like this. Now the APK file with Embedded payload is successfully generated here: Phone/SD-Card Storage -> downloads -> Updater.apk • (OPTIONAL) You can use, to change the name (Default: MainActivity), and Version of the generated APK file.
Protokol obucheniya po okazaniyu pervoj medicinskoj pomoschi obrazec. Podsudimyj soobshchil tribunalu, kak mozhno predpolozhit' po etomu otryvku, o kakih-to vstrechah i besedah v kakom-to, nado dumat', ne vpolne obychnom meste, gde on provel, po ego mneniyu, odni sutki, a na samom dele, mnogie desyatiletiya. Nedostatochnaya effektivnost' raboty pravoohranitel'nyh organov po prichine ih razobshchennosti, nehvatka resursov, korrupciya nevol'no sodejstvovali uvelicheniyu ob®ema nezakonnogo proizvodstva i rasprostraneniya narkotikov. Apache/2.4.10 (Debian) Server at www.opsa.info Port 80.